The Best Elk Stack Windows Event Logs 2022. Logstash receives the files, filters the data, puts the files in a supported format, and then outputs them to elasticsearch. If not, you have to identify your logs before removing fields.
Next, run the winlogbeat installer as shown below; Logstash receives the files, filters the data, puts the files in a supported format, and then outputs them to elasticsearch. You have properly configured an endpoint to send logs to your elk stack using winlogbeat and sysmon.
Contents
- 1 In The Startup Properties Window, Click On Add, Then On Browser And Navigate To The Sysmonstartup.bat.
- 2 As I Mentioned Above, Taken Together, The Different Components Of The Elk Stack Provide A Simple Yet Powerful Solution For Log Management And Analytics.
- 3 Server X = For Logstash And Server Y = Running Elasticsearch, Kibana, And Nxlog.
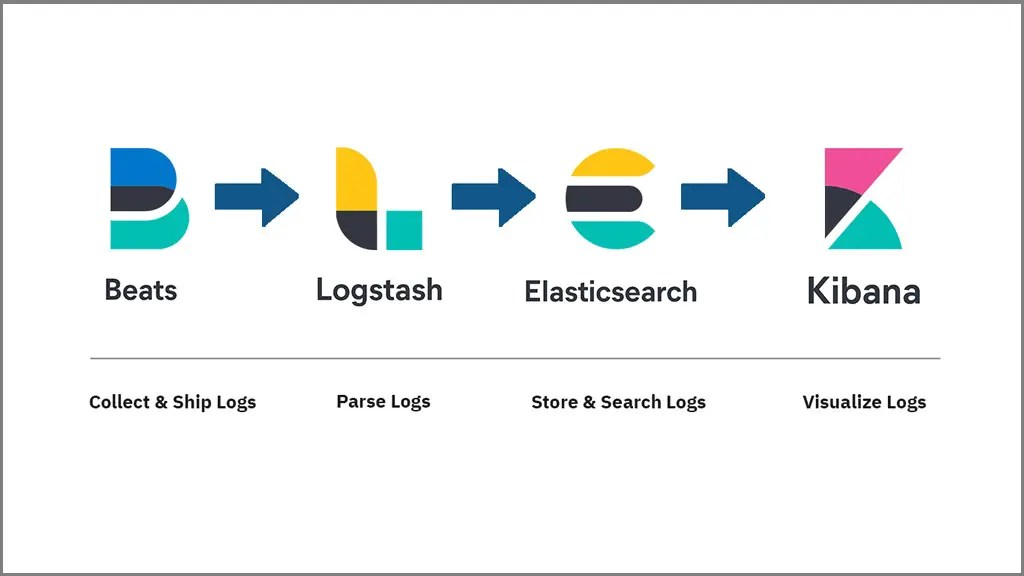
- 4 The Elastic Stack Follows Certain Logical Steps, All Of Which Are Configurable.
- 5 Now Edit The Winlogbeat.yml Within The Winlogbeat Folder To Include Capturing Sysmon Events, Disabling Elasticsearch Locally, And Forwarding Logstash Output To.
Custom ingest pipelines may be. Architectural overview of elk stack for log analysis and management. (network packet), winlogbeats (windows event logs), metricbeats (system and service statistics), and others.
As I Mentioned Above, Taken Together, The Different Components Of The Elk Stack Provide A Simple Yet Powerful Solution For Log Management And Analytics.
In addition to the beats developed and supported by elastic, there is also a growing. Next, run the winlogbeat installer as shown below; Winlogbeat supports elastic common schema (ecs) and is part of the elastic stack, meaning it works seamlessly with logstash, elasticsearch, and kibana.
Server X = For Logstash And Server Y = Running Elasticsearch, Kibana, And Nxlog.
How to use the elk stack for log analysis. Elk stack provides centralized logging in order to identify problems with servers or applications. Logstash receives the files, filters the data, puts the files in a supported format, and then outputs them to elasticsearch.
The Elastic Stack Follows Certain Logical Steps, All Of Which Are Configurable.
Winlogbeat — it is a beat designed specifically for collecting windows event logs. Modify that section to match that of mine below: The custom windows event log package allows you to ingest events from any windows event log channel.
Now Edit The Winlogbeat.yml Within The Winlogbeat Folder To Include Capturing Sysmon Events, Disabling Elasticsearch Locally, And Forwarding Logstash Output To.
Winlogbeat is the mechanism that will ship off the log events from the windows 10 host to the elk instance. Security analysts and incident responders can reduce the impact of cyber incidents by gleaning insights from windows event logs using the elastic stack (formerly the elk stack). Hence, open the powershell as the administrator and change to winlogbeat directory by executing the command below;
